package dk.topsecurity.server;
import javax.security.auth.Subject;
import javax.security.auth.callback.Callback;
import javax.security.auth.callback.CallbackHandler;
import javax.security.auth.callback.NameCallback;
import javax.security.auth.callback.PasswordCallback;
import javax.security.auth.login.LoginContext;
import javax.security.auth.login.LoginException;
import dk.topsecurity.common.TopsecurityLoginInterface;
import dk.topsecurity.common.TopsecurityServerInterface;
/**
* Implements the server object that allows clients to login.
*/
public class TopsecurityLoginImpl
extends java.rmi.server.UnicastRemoteObject
implements TopsecurityLoginInterface
{
/** The real server object
*/
private TopsecurityServerInterface myServer;
/**
* Class constructor.
*
* @param theServer The real server object.
*/
public TopsecurityLoginImpl(TopsecurityServerInterface theServer)
throws java.rmi.RemoteException {
myServer = theServer;
}
/**
* Allows a client to login and get an interface to the server.
*/
public TopsecurityServerInterface login(String username, String password)
throws java.rmi.RemoteException, LoginException {
LoginContext lc = new LoginContext("TopsecurityJAASLogin", new RemoteCallbackHandler(username, password));
lc.login();
Subject user = lc.getSubject();
// Return a reference to a proxy object that encapsulates the access
// to the server, for this client
return new TopsecurityServerProxy(user, myServer);
}
}
class RemoteCallbackHandler implements CallbackHandler {
private String username;
private String password;
RemoteCallbackHandler(String username, String password){
this.username = username;
this.password = password;
}
public void handle(Callback[] cb) {
for (int i = 0; i < cb.length; i++){
if (cb[i] instanceof NameCallback){
NameCallback nc = (NameCallback)cb[i];
nc.setName(username);
} else if (cb[i] instanceof PasswordCallback){
PasswordCallback pc = (PasswordCallback)cb[i];
pc.setPassword(password.toCharArray());
password = null;
}
}
}
}
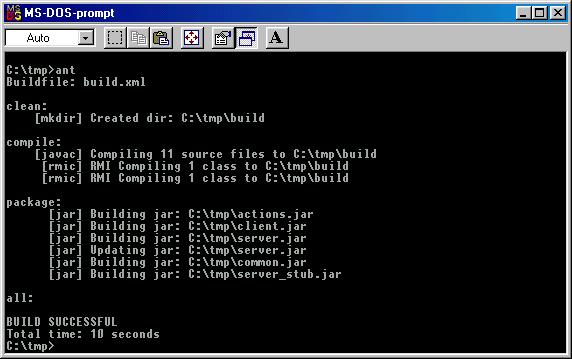
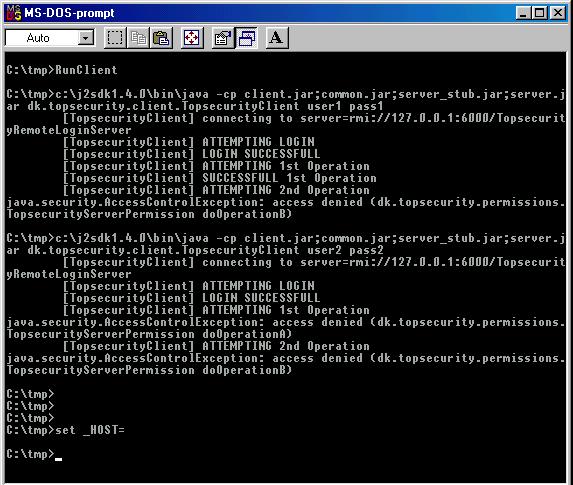
 . Here
the "proxy" is operating more or less entirely a client concept. The server
sends back a stub for ServerImpl which is enrolled in a proxy on the client.
His scope is different.. but I don't completely approve of his strategy
anyhow. But read and make your own opinion.
. Here
the "proxy" is operating more or less entirely a client concept. The server
sends back a stub for ServerImpl which is enrolled in a proxy on the client.
His scope is different.. but I don't completely approve of his strategy
anyhow. But read and make your own opinion.