setmqaut syntax
>>-setmqaut--- -m QMgrName--- -n ObjectName--- -t ObjectType---->
.--------------------------.
V |
>-----+----------------------+-------+- -p PrincipalName-+--+--->
'- -s ServiceComponent-' '- -g GroupName-----'
.------------------------------------------.
V |
>---------+-| MQI authorizations |------------+--+-------------><
+-| Context authorizations |--------+
+-| Administration authorizations |-+
'-| Generic authorizations |--------'
MQI authorizations
.-----------------------.
V |
|---------+- +get -----+----+-----------------------------------|
+- -get -----+
+- +browse --+
+- -browse --+
+- +put -----+
+- -put -----+
+- +inq -----+
+- -inq -----+
+- +set -----+
+- -set -----+
+- +connect -+
+- -connect -+
+- +altusr --+
'- -altusr --'
Context authorizations
.-----------------------.
V |
|---------+- +passid --+----+-----------------------------------|
+- -passid --+
+- +passall -+
+- -passall -+
+- +setid ---+
+- -setid ---+
+- +setall --+
'- -setall --'
Administration authorizations
.-------------------.
V |
|--------+- +crt -+----+----------------------------------------|
+- -crt -+
+- +dlt -+
+- -dlt -+
+- +chg -+
+- -chg -+
+- +dsp -+
+- -dsp -+
+- +clr -+
'- -clr -'
Generic authorizations
.----------------------.
V |
|---------+- +allmqi -+----+------------------------------------|
+- -allmqi -+
+- +alladm -+
+- -alladm -+
+- +all ----+
'- -all ----'
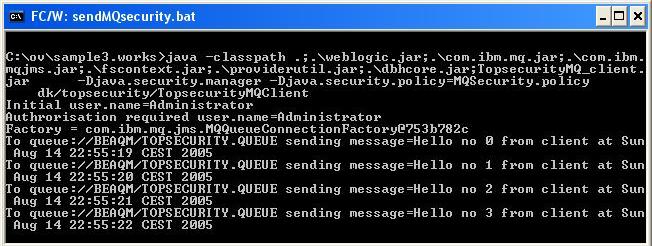
setmqaut example
setmqaut -m "topsecurity.queue.manager.name" -t queue -n topsecurity.queue.name -g topsecuritygroup +allshould give all rights to the queue "topsecurity.queue.name" defined with queuemanager "topsecurity.queue.manager.name" where topsecuritygroup is the ID of the group to be given the authorizations.
TopsecurityMQClient.java |
|
|
MQSecurity.policy |
sendMQsecurity.cmdset BEA_HOME=C:\bea set WL_HOME=C:\bea\weblogic81 java -classpath .;.\weblogic.jar;.\com.ibm.mq.jar;.\com.ibm.mqjms.jar;.\fscontext.jar;.\providerutil.jar;.\dbhcore.jar;TopsecurityMQ_client.jar -Djava.security.manager -Djava.security.policy=MQSecurity.policy dk/topsecurity/TopsecurityMQClient |